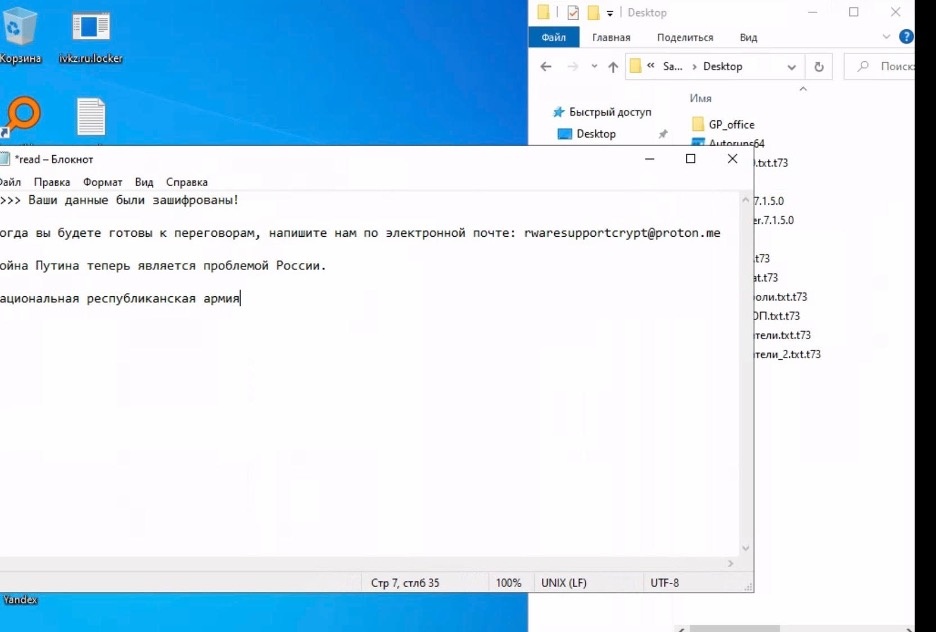
The National Republican Army (NRA) of Russia is seeking the overthrow of Vladimir Putin’s regime. On Oct. 17, Kyiv Post was sent information indicating that a massive breach of Russia’s defense and intelligence contractors may have taken place.
In perhaps one of the largest IT-security breaches in Russian history, Kyiv Post was contacted on Oct. 17 by hackers who indicated that they were supporters of the Russian NRA. As Kyiv Post has previously reported, the NRA is an organization of Russian opposition members seeking the overthrow of the Putin regime, including via the use of violent means.
- Access the newest Ukraine news items published today.
- Access the newest Ukraine news items published today.
- Russian Losses in Ukraine
JOIN US ON TELEGRAM
Follow our coverage of the war on the @Kyivpost_official.
The NRA-affiliates told Kyiv Post that they had hacked several major Russian technology firms that are currently providing services critical to the Russian Government’s national security. The hackers provided Kyiv Post with exclusive access to a large volume of documents and photos which they said came from the internal servers of companies which the NRA-hackers believe are making Russia’s war possible.
Technoserv
One of the reportedly hacked businesses is Technoserv – Russia’s largest systems integrator – which operates in various countries in a consultancy capacity. The company is headquartered in Moscow, has an estimated net revenue of $107 million, and is owned by brothers Dmitry and Alexei Ananyev. According to a 2022 article in the The Belfast Telegraph, the brothers also own Promsvyazbank. The article states that “according to UK Government sources, [the bank] now services 70 percent of state contracts signed by Russia’s defense ministry and is a ‘pivotal bank’ for the country’s military industrial complex.”

Zelensky Condemns Russian ‘Inhumane’ Christmas Attack on Energy Grid
A Russian businessman who formerly worked in the Russian IT sphere with government contracts, told Kyiv Post that it seemed likely the hackers had “access to the architecture networks, databases, cloud solutions, and other information that is of key importance to the Russian Government.”
He added that what the hackers stood to gain would likely be “significant” as Technoserv is known as “the people who are the architects of the Russian Government.”
Using data stolen during this hack, the businessman confirmed that the hackers could “begin serious breaches across large swathes of the Russian Government – a very serious breach.”
The hackers provided Kyiv Post with a trove of documents, files, and screenshots. Among these was a screenshot note, apparently left for Technoserv’s system administrator, which in English translates as:
“Technoserv,
You have been hacked due to your close cooperation with the Russian Government, which has staged a war.
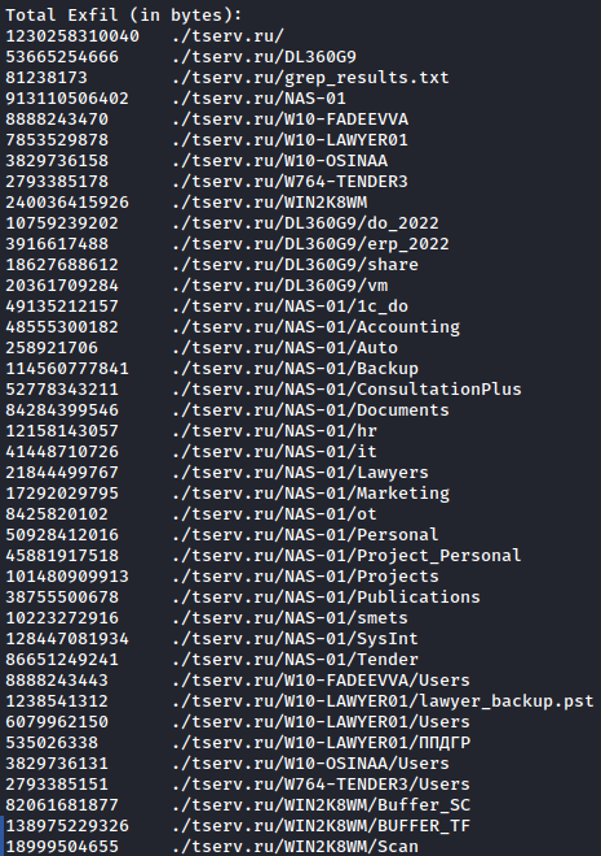
We’ve received over 1.2 TB of data from every computer and server on your network.
The data contains everything from AutoCAD designs, contracts with clients and partners, employees’ personal information (phone numbers and addresses, passport details, photographs, etc.).
After summing up the calculation, we have determined that we have seized 1,081,892 files from you.
You have very little time to respond to this letter and agree on terms with us. If you do not contact us, all these files will be published on the Internet and available to everyone free of charge.
As a demonstration that we have, in fact, received the amount of data that we claim, here is proof. Files were selected randomly.
http://z2w5lrrj2yawsrb7lue6ws25ihlxz2ddr7uimwnkdm7sym4jx5bt3gid.onion:8080/tserv.ru/
We hope you know how to use Tor, but just in case, here’s a link for you:
https://www.torproject.org/ru/download/
There are no innocents! Therefore, carefully consider your next steps, we will not wait too patiently for your answer.
The National Republican Army (of Russia)”
Among other documents provided to Kyiv Post, which the NRA hackers said came from the internal servers of Technoserv, were documents indicating a relationship between the Federal Security Service (FSB) of Russia and Technoserv.
The NRA-affiliated hackers told Kyiv Post that the breach includes “Network Attached Storage” (NAS). This refers to a storage server connected to a computer network that is capable of holding a significant amount of data. If hackers are indeed able to exploit such a server, they could obtain data from right across the network.
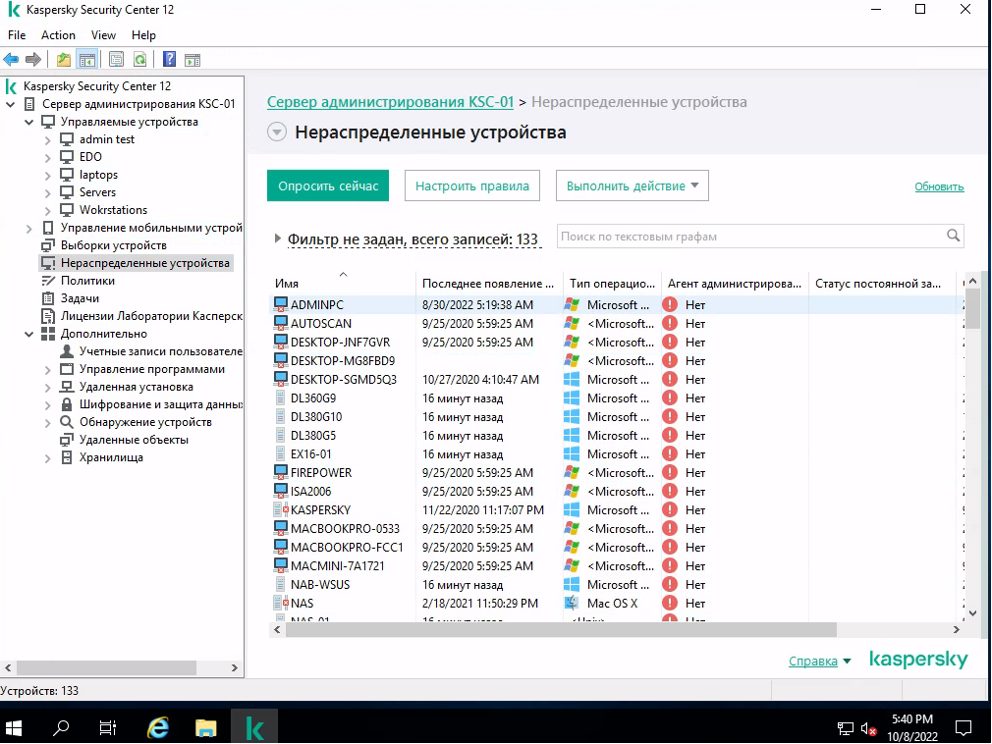
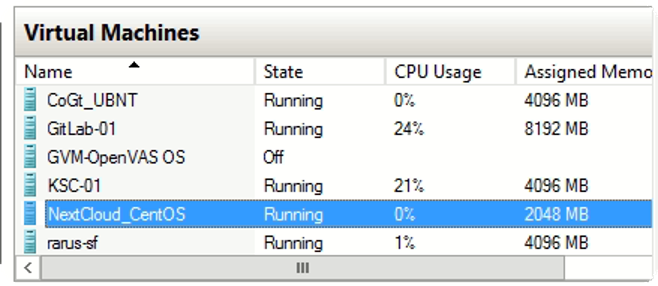
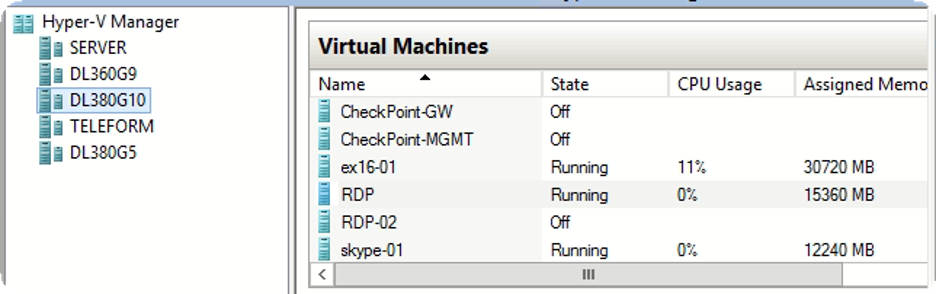
The hackers provided Kyiv Post with photos that allegedly demonstrate their administrative access to the company’s “Kaspersky Security Center 12” and virtual machines maintained through “Hyper-V Manager.”
Kaspersky, a large Russian anti-virus firm, has been previously accused of directly collaborating with Russian intelligence to scan and take data from Russian Government opponents. Thus, the potential use of Kaspersky in this hack could support the NRA’s own assertions that scorned Russian intelligence agents are turning rogue on the Putin regime and are in fact the orchestrators of some of the NRA’s attacks.
NRA-affiliated hackers also sent Kyiv Post several screenshots indicating that they had taken-over the websites of various other Russian Government service providers. When the Kyiv Post sought to check the contractors’ websites, a large logo of a woman with a white-blue-white flag, a common symbol of the Russian opposition to Putin, was the only item found on the sites.
The Russian Government has not yet publicly commented on the NRA’s reported hacks. However, if the hacks against contractors working for Russia’s defense were in fact undertaken by rogue members of Putin’s trusted intelligence services, it would represent a significant blow to the Putin regime.
You can also highlight the text and press Ctrl + Enter